Most simulations contain social engineering since attackers usually Incorporate the two for any simpler marketing campaign. Simulations mirror actual-earth phishing eventualities, but personnel activity is monitored and tracked.Once you put an purchase, you can established your password and login to your account and dashboard. You can buy far more
 Jonathan Taylor Thomas Then & Now!
Jonathan Taylor Thomas Then & Now!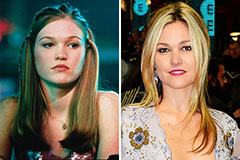 Julia Stiles Then & Now!
Julia Stiles Then & Now! Elin Nordegren Then & Now!
Elin Nordegren Then & Now!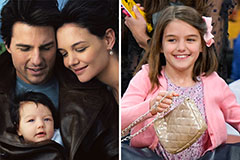 Suri Cruise Then & Now!
Suri Cruise Then & Now!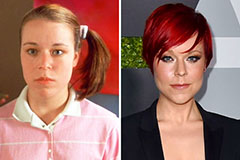 Tina Majorino Then & Now!
Tina Majorino Then & Now!